This data enables autonomous or assisted flight, making operation easier, and increasing accessibility. As a result, drones have become part of the smart mobility offerings that are now commercially available to businesses and consumers. This technology enables drones to detect objects while flying and allows the analysis and recording of information on the ground.

Army developed the experimental Kettering Bug, an unmanned “flying bomb” aircraft, which was never used in combat. Television networks use drones to capture sporting event footage, such as taped and live flyover footage, that would otherwise be difficult to capture. Federal Aviation Administration regulations, as well as sports league, venue and local law enforcement agency rules. Navigational systems, such as GPS, are typically housed in the nose of a drone.
The FAA estimates that birds cause more than $1 billion in damages to aircraft in the United States. Trevir Nath has five years of experience as a financial writer working with various startups, financial services companies, and news publications. Trevor is an expert on business, personal finance, and trading. https://globalcloudteam.com/ If the question is about building a drone, I would say it depends on the hardware used to build it. Communication between microcontoller and all other sensors is established so that the controller can process the sensor readings and sends control signals to actuators to achieve a stable flight.
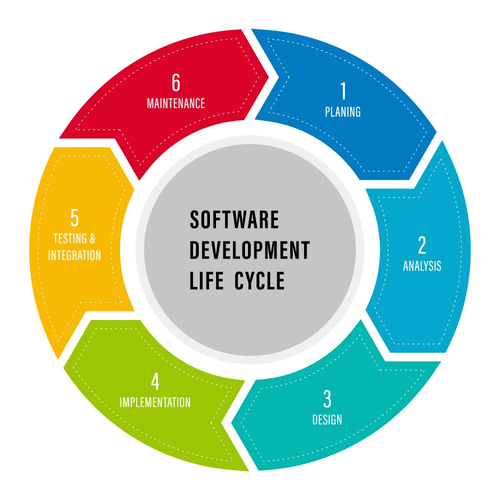
What Is A Drone?
Between drone service providers and business-internal services, there are more than 30 companies using drones to deliver medical supplies. With companies learning how to incorporate drone technology into their vital business processes, the career opportunities in the field of small unmanned aerial systems or vehicles are bound to increase. Drones have got several names in the present technological era, such as a mini flying robot, unnamed aerial vehicles, mini pilotless aircraft, and more. Regardless of the name you call it, the drones are powering up very rapidly taking over most of the business industries. The defense is known to be untouched by most of the IT solutions but drones are the only element that has made strong and irreplaceable importance in the defense sector.
The Career Services Office assists NEIT students and graduates in all aspects of the job search, including resume writing, interviewing skills, and developing a job search strategy. Upon completion of their program, graduates may submit a resume to the Career Services Office to be circulated to employers for employment opportunities in their fields. In addition, our Career Services Office contacts employers to develop job leads. A strong relationship with employers exists as a result of our training students to meet the needs of industry for over fifty years. No school can, and NEIT does not, guarantee to its graduates’ employment or a specific starting salary.

The on-time support of vaccination and medication can help in reducing the number of infections and save masses of human lives. The mission of the Electronics, Robotics and Drones Technology program is to prepare individuals for entry-level employment as technicians, designers, or operators in electronics, robotics, drone technology and automation. Unlike what most drone technology industry professionals believe, drones need not have autonomous flight capabilities. While online retailers are more convenient, purchases of goods and services are subject to additional shipping and handling charges incurred by the consumer. Even though technology has transformed a number of industries over the past 10 years, shipping and postage have remained relatively unchanged. Traditional postal service providers such as USPS, UPS , and FedEx have remained the primary source of shipping and handling for major online retailers.
Unmanned Aerial Vehicles, Uavs, Are Becoming More And
Rapid adoption of drones over the past decade has sparked privacy, security and safety complaints and concerns. Voyeurs and paparazzi use drones to obtain images of people in their homes and other locations once assumed to be private. Drones are also used in unsafe locations, such as urban areas and near airports. Beyond surveillance and delivery applications, UAVs are used for drone journalism, search and rescue, disaster response, asset protection, wildlife monitoring, firefighting, communications relay, healthcare and agriculture. Tethered systems can solve the power-supply challenge many drones face if the tether provides a direct power supply. For example, Elistair’s Safe-T drone tethering station offers 2.5 kW power and can fly to heights of more than 200 feet, with data transfer rates of up to 200 Mbps.
They are working on short term field studies focused on s pecific regions of the US to study how terrain and land surface features affect weather patterns. The goal is to determine whether and how the land surface impacts weather, and how to incorporate that variable into weather and climate models. The lowest layer of the atmosphere, called the boundary layer, is drone software development where most of our weather is happening. The weather conditions that impact each and every one of us are dependent on a dizzying number of variables and factors. Trying to make accurate predictions about what the weather will do next relies on very complicated weather forecasting models, but the output of these models is only as good as the data fed into them.
It also sells to construction, utilities telecom and public safety businesses. From logistics to agriculture to security, unmanned aerial vehicles and IoT are often part of the same discussion. They offer a component in ubiquitous connectivity and interactivity. The integration of drones and internet of things technology has created many enterprise applications. Cloud based web application for drone fleet management, performance monitoring, mission planning, real-time control and post flight AI analytics.

The adoption of drone technology has not achieved a mass quantity but it has started transforming the traditional rigid solutions making it more technological. The UAV services are more beneficial in remote locations with little or poor transportation infrastructure . In case of strict lockdown or curfew, the drone can also be utilized for providing food and other essential products to the most afflicted COVID-19 zones. The camera implanted on the UAVs may also facilitate monitoring the real-time picture of lockdown and curfew enforced in various parts of the country. It can also be used as a surveillance tool for quarantined victims. These robotic tools will also be beneficial in spying or monitoring cinema halls, marriage palaces and other crowded areas to enforce strict social distancing rule governed by the government.
Drones can be equipped with sensors, including ultrasonic, laser or lidar distance sensors, time-of-flight sensors, chemical sensors, and stabilization and orientation sensors. Red, green and blue sensors collect standard visual red, green and blue wavelengths, and multispectral sensors collect visible and nonvisible wavelengths, such as infrared and ultraviolet. Accelerometers, gyroscopes, magnetometers, barometers and GPS are also common drone features.
The GPS on a drone communicates its precise location to the controller. The altimeter also helps keep the drone at a specific altitude if the controller designates one. Drones require a controller, which lets the operator use remote controls to launch, navigate and land the aircraft. Controllers communicate with the drone using radio waves, such as Wi-Fi.
A security tech company teamed with a drone startup to hunt for Zigbee beacons to provide an overview of the IoT networks present in residential and business areas of the city. The companies reported that the results were quick and instructive. Stronger, more capable drones are also available for use in commercial settings. Insitu, a Boeing company, offers the ScanEagle, a UAV with a 10-foot wingspan and weighs 35 pounds.
For landing, drones use visual positioning systems with downward-facing cameras and ultrasonic sensors. The ultrasonic sensors determine how close the drone is to the ground. Ability to perform learned skills, independently, with accuracy and completeness within reasonable time frames in accordance with procedures.
Impact Of Technology On Health Care Sector
To implement neural networks in drones, researchers must first train the machine learning algorithms to recognize and correctly classify objects in a wide variety of contexts. This is done by feeding specially marked images into the algorithm. Grandview Research has predicted revenue from the commercial drone market will reach $501.4 billion in 2028, up from $20.8 billion in 2021. For example, a Remote Pilot Certificate issued by the FAA is required to fly drones commercially and commercial UAVs must be registered and flown at or under 100 mph. Both recreational and commercial pilots are limited to a maximum height of 400 feet. A 2015 experiment in Austin, Texas, showed one way to combine drones and IoT.
Before sharing sensitive information, make sure you’re on a federal government site. Acute enough to read dials, and position of control settings of electronics testing equipment and operational controls. Almost half of your technical courses consist of laboratory work.

On the other hand, headwinds or tailwinds can even have a slightly positive effect on energy consumption. In 2014, two planes had gone missing with no luck at finding the wreckage. Lives were lost and families are left wondering “what happened? In the world of truly autonomous vehicles, UAVs should react on their own through some sort of external stimuli. It is through these external stimuli that the UAVs react and adjust their goal accordingly. These stimuli can be taken from various sensors on the craft but also can be given commands by a human.
Government authorities as well as insurers are waking up to the potential of using them to assess post-disaster damages, especially at sites not marked safe for humans to enter. Chief data officers are taking on additional responsibilities beyond data management as they strive to transform organizations’ … Blockchain is most famous for its cryptocurrency applications, but data centers can employ it for a variety of business-related … As drones continue to gain popularity in the enterprise, integration with well-constructed enterprise IoT networks will become increasingly important. Learn the 7 components of developing IoT infrastructure in the enterprise. In China, flying higher than 400 feet requires a drone license from the Civil Aviation Administration of China.
Program Mission, Goals, And Outcomes
An official transcript from the other institution must be received before the end of the first week of the term for transfer credit to be granted for courses to be taken during that term. Students will receive a tuition reduction for the approved technical courses based on the program rate and will be applied against the final technical term of the curriculum’s tuition amount. No tuition credit is provided for courses which are not a part of the technical curriculum. Initially drones have seen early adoption in Surveillance and Security, Mapping and Inspection and Detection industries because of the remote locations they have been easier to deploy there.
- The FAA gradually modifying Part 107 of the Small Unmanned Aircraft Systems Regulation.
- Drones can be equipped with various types of surveillance equipment that can collect HD video and still images day and night.
- Depending on the state, personal drone users may need to pass a safety test or obtain a license.
- Drones will also introduce new security vulnerabilities and attack vectors.
- Fixed-wing, which include the hybrid vertical takeoff and landing drones that don’t require runways.
Likewise, states will benefit from tax windfalls, stemming from increased economic activity. Powered by batteries, drones are more environmentally friendly than delivery trucks. If delivery drones gain widespread usage, this would reduce the reliance on vehicles for many companies.
Training In Drone Technology
They use lidar remote sensing technology that illuminates the crop with a laser and calculates distance by measuring what is reflected back. This can help farmers optimize agricultural production and promote sustainable farming practices. In 2018, Boeing announced it had prototyped an unmanned electric VTOL cargo air vehicle capable of transporting up to a 500-pound payload. DJI Mini 2, at about 242 grams, it’s one of the lightest drones.
Commercial And Enterprise Drone Applications
Programming to build a drone is different from programming to make a drone perform some tasks. Building a drone involves interfacing sensors and actuators with some kind of processor to make the drone fly stably. But, to make an application all needed is a readily available drone and a computer where algorithms can be implemented. There are several applications in which delivery drones are used.
Q&a And Technical Standards
Commercial drones will also allow industries to realize savings from cost-effective means of inventory, transportation, and distribution. These cost savings can be passed down to the consumer through a reduction in prices. For example, municipalities in Arizona that have two or more public parks must allow drones in at least one of them. A Minnesota law requires commercial drone operators to pay a commercial operations license and have drone insurance. Depending on the state, personal drone users may need to pass a safety test or obtain a license.
We are right on track to a final destination where drones will eventually be self-sufficient. But even if this particular system has not yet proved itself in the wild, it’s a clear illustration of the direction contemporary research is going. Using AI to identify body poses is a common problem, with big tech companies like Facebook publishing significant research on the topic. And with the rise of cheap drones and fast mobile internet, it’s easier than ever to capture and transmit live video footage.
Ability to concentrate for long periods of time and retain information on intricate details of component theory and analysis/operation of electronics circuits. New England Institute of Technology is the proud recipient of a grant from the Feinstein Foundation. To satisfy the terms of the grant, the university has developed a one-credit community enrichment course which includes hands-on community enrichment projects. The course can be taken for a few hours per term, spread over several terms. Students who are already engaged in community enrichment on their own may be able to count that service towards course credit.